10 steps to a safer Web3 experience
Web3 can feel like the wild west to new users. Learn how to navigate the crypto space without hassle in a safer manner.
By Sankrit K

Web3, the next iteration of the internet, is changing how we interact with digital assets, data, and applications. Powered by blockchain and decentralized protocols, it enables trustless transactions, computation, and data storage.
The emergence of cryptocurrencies, non-fungible tokens (NFTs), and decentralized finance has created new opportunities for users to participate in a global economy without intermediaries or central authorities.
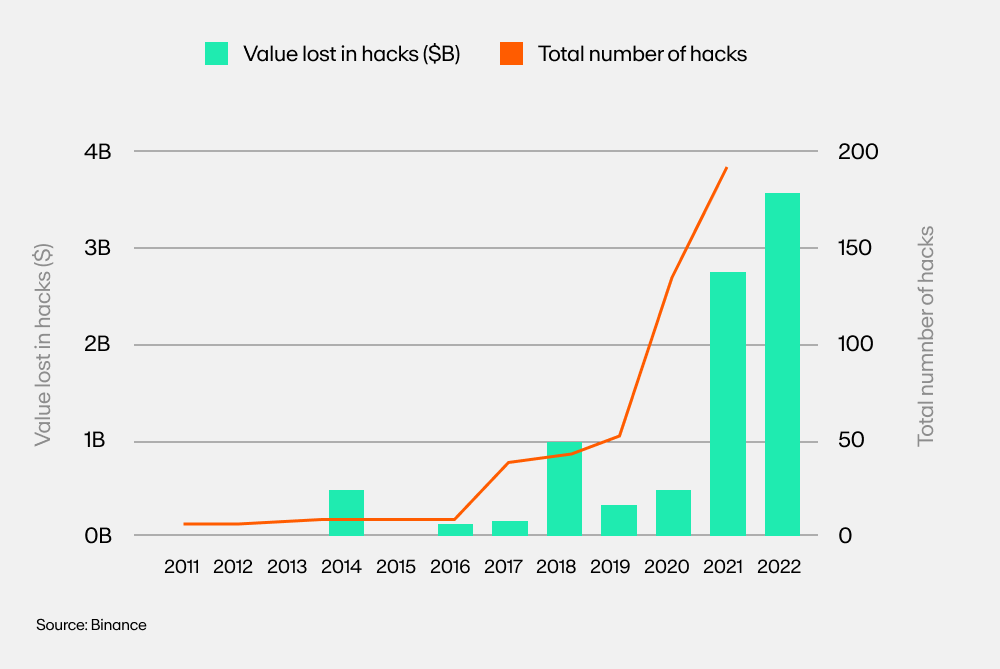
With this new frontier, however, comes new challenges and risks. According to several reports, the monetary value lost due to hacks has risen exponentially from just under $1 billion in 2018 to $4 billion in 2022, with $343 million stolen just last month in November 2023.
These alarming statistics highlight the need for individuals who want to participate in Web3 to take available precautions and try to stay safe.
This article covers 10 helpful steps you can take to protect yourself while buying and selling cryptocurrencies and NFTs.
1) Keep your private keys off the grid
Private keys are the most important part of owning crypto assets. If lost or stolen, your funds could be gone forever. Make sure to back them up securely offline and never share them with anyone, no matter how trusted they may seem.
Ways to store your private keys:
- Memorize them
- Write them on a piece of paper
- Use storage devices like Cryptotag
Pro tip: You should never store private keys digitally.
2) Practice self-custody
At MoonPay, we strongly advocate for the self-custody of your assets.
Self-custody of assets is the act of securely storing your crypto and NFTs in a non-custodial wallet. It means that you have complete control over your funds and private keys with no third-party access. Self-custody offers more security and privacy than custodial wallets but does require some technical knowledge to operate them.
Self-custody also places more responsibility on the individual, who is solely in control of their private keys.
Some popular choices for self-custody wallets are hardware wallets like Ledger and Trezor, desktop wallets such as Electrum and Atomic, or mobile wallets like MetaMask.
3) Enable Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is one of the most important security measures for protecting your wallet and funds. 2FA requires that users enter a code, which is sent to their phone or email account, in addition to their login credentials.
This makes it much harder for malicious actors to access your account.
Most wallets and cryptocurrency exchanges support 2FA, and it is always a good idea to enable this feature.
Additionally, you should consider setting up multiple layers of 2FA, if possible, for extra security. This can include two-step verification (2SV) with security keys or authenticator apps, as well as SMS and email notifications.
4) Verify the integrity of smart contracts before interacting with them
Smart contracts are computer programs executed on the blockchain, allowing for the trustless and automated execution of agreements. It is crucial to verify the integrity of a smart contract before interacting with it, as some contracts may contain malicious code that can cause you to lose funds.
You can use tools like Etherscan or Cyberscan to audit the code of a smart contract and check for potential vulnerabilities. Another way to check the integrity is to use a trusted service that verifies smart contracts, such as Quantstamp.
5) Only interact with reputable services and platforms
In addition to verifying the integrity of smart contracts, it is also important to interact with only reputable services and platforms. Researching the company behind any product or service can help identify potential red flags.
You should also verify the legitimacy of any website you visit, as there may be malicious actors looking to take advantage of unsuspecting users. Look for the HTTPS in the URL bar or a padlock icon next to it to make sure that you are connecting with an authentic site. Additionally, only use services from sites that you trust.
6) Read transaction messages before authorizing
One of the biggest risks of interacting with smart contracts on the blockchain is the possibility of unexpected or unauthorized interactions.
When you interact with a decentralized application (dApp) or sign in using your cryptocurrency wallet, you may be asked to authorize a transaction. It is always important to check the message associated with the transaction request before authorizing it.
The message will provide more information about the action you are taking and should be read through carefully. Some applications ask for permission to take action on your behalf. If the app is malicious, it may execute a transaction on your behalf that would drain all your funds.
7) Use decentralized identities
Decentralized Identifiers (DIDs) can help secure your identity and data on the blockchain.
DIDs are cryptographic identifiers that exist independently from any central authority or third-party service provider. This allows users to control their own data while also making it easier for applications to comply with Know Your Customer (KYC) regulations.
Further, DIDs are cryptographically secure and immutable, which makes them more resistant to identity theft or data tampering. As such, they can enable a more secure digital ecosystem that better protects user privacy.
8) Be mindful of market liquidity when trading
When trading cryptocurrency or NFTs, it is important to be mindful of the market’s liquidity.
Liquidity refers to how quickly you can buy and sell an asset without significantly impacting its price. Low liquidity can cause prices to become volatile, and your transactions may not execute as quickly as you expect.
For example, cryptocurrencies like Bitcoin or Ethereum are very liquid, as there is always a good chance of finding buyers for them. NFTs, on the other hand, might be classified as illiquid assets because there is often limited demand for them.
It is important to research the liquidity of an asset before trading it and to consider using limit orders rather than market orders when trading because limit orders provide greater control over your entry and exit points.
9) Always have an exit strategy
Always have an exit strategy when investing or trading. Even if you are confident in your investment, it is important to consider the potential risks before entering a position.
When creating an exit strategy, set clear entry and exit points for yourself so that you know when to buy and sell. Additionally, it can be helpful to create a plan for how you will handle losses or market downturns.
Also remember that the markets are unpredictable, and anything can happen at any time.
10) Set slippage to avoid sandwich attacks
“Slippage” is the difference between your requested price for buying or selling an asset and the actual executed price. When trading on any decentralized exchange, slippage is one of the most important parameters to keep in mind.
A sandwich attack occurs when a malicious trader places large orders at two different prices before and after yours, resulting in yours getting filled at a price much higher or lower than expected. DEXs allow you to choose your desired slippage before executing a trade. This can help mitigate the risk of falling prey to a sandwich attack.
Pro tip: Setting your slippage to 0.5 - 2% can help you avoid such situations and protect yourself from losses.
The lower the slippage, the less likely your order will execute at a price much higher or lower than expected. At the same time, setting a very low slippage might keep your transaction from being fulfilled, as there might not be enough liquidity to execute your transaction.
Avoid crypto scams
Crypto is revolutionizing the way that value is exchanged, but its rapid growth has also created opportunities for malicious actors.
Read our article How to spot and avoid crypto scams to learn about some of the most common scams and how to spot them.