Blockchain technology has become a cornerstone of the digital revolution, offering a decentralized approach to data management and transactions.
It has revolutionized the financial system by introducing decentralized networks where no single entity holds control. This decentralization relies on cryptographic techniques that safeguard data security and integrity, allowing participants to trust the ledger without requiring a central authority to verify transactions.
There are several types of blockchain networks, with more to be developed as the technology evolves. The two most prominent types are permissioned and permissionless blockchains, each catering to different needs, trade-offs, and use cases. So, what sets them apart?
In this article, we’ll dive into the key differences, use cases, advantages, and challenges of each type of blockchain, helping you determine which one might be best suited for your needs.
What is a Permissioned Blockchain?
A permissioned blockchain is a type of blockchain that requires approval to access the network. Unlike public blockchains, where anyone can join, permissioned blockchains restrict access to specific members. These participants are usually verified by a central authority that manages the network.

In a permissioned network, a central entity has control over the blockchain's governance, deciding who can read the ledger, execute transactions, and participate in the consensus process. This level of control is often necessary for industries that require strict compliance with regulatory standards or where sensitive data is involved.
Another defining feature of permissioned blockchains is their use of customizable consensus mechanisms. Unlike open blockchains that often rely on energy-intensive methods like Proof-of-Work (PoW), permissioned blockchains can implement more efficient consensus algorithms. Some popular options include Practical Byzantine Fault Tolerance (PBFT) and Raft, which are better suited for environments with known participants.
Key characteristics of permissioned blockchains
- Restricted access: Only authorized participants can join and transact on the network.
- Centralized governance: Typically governed by one or a few organizations.
- Participant control: Network administrators control who can read, write, or validate transactions.
- Scalability: Often designed for higher efficiency and scalability compared to public blockchains.
What is a Permissionless Blockchain?
A permissionless blockchain is a public blockchain open to anyone who wants to join the network. There is no central authority controlling access, and participants can freely view the ledger, execute transactions, and participate in consensus. Some prime examples include popular blockchains like Bitcoin and Ethereum.

In a permissionless blockchain, the network is maintained by a decentralized group of participants, often referred to as nodes. These nodes work together in verifying transactions and maintaining the integrity of the blockchain. Like most blockchains, permissionless networks also employ consensus algorithms like Proof-of-Work (PoW) or Proof-of-Stake (PoS) to ensure that all participants agree on the state of the ledger.
Even more than other network types, permissionless blockchains are designed to be transparent, with all transactions and data publicly accessible. Anyone across the globe can verify the data recorded on the blockchain, making it a trustless system where network participants do not need to rely on a centralized authority to ensure the validity of transactions.
Key characteristics of permissionless blockchains
- Open access: Anyone can join the public network and participate in transaction validation.
- Decentralized governance: The network is governed by a consensus protocol without a central entity.
- Transparency: All transactions are publicly visible on public blockchains.
- Decentralized security: The security of the network is enhanced by its decentralized nature.
Main Differences Between Permissioned and Permissionless Blockchains
The key difference between permissioned and permissionless blockchains is access and governance.
Permissioned blockchains restrict participation to verified members, making them suitable for private, regulated industries. Permissionless blockchains are open to anyone, ensuring transparency, decentralization, and global accessibility.
Each model offers distinct trade-offs in security, scalability, and control, among other criteria:
Feature | Permissioned Blockchain | Permissionless Blockchain |
Access Control | Restricted to verified participants | Open to anyone |
Governance | Centralized | Decentralized |
Transparency | Limited | High |
Security | High (due to restricted access) | High (due to decentralization) |
Transaction Speed | Generally faster | Can be slower |
Scalability | Limited | Varies, often challenged |
Energy Consumption | Generally lower | Often higher (e.g., in proof-of-work systems) |
Use Cases | Enterprise, Consortiums | Cryptocurrencies, Decentralized Applications |
Pros of Permissioned Blockchains
Permissioned blockchains offer several benefits that make them viable for certain enterprises and regulated industries.
Enhanced privacy and confidentiality
Permissioned and private blockchains provide controlled access to the network, ensuring that only authorized participants can view and interact with data. This could make them suitable for industries like finance and healthcare, where protecting sensitive information is critical.
Scalability and efficiency
Due to their controlled environments and optimized consensus mechanisms, permissioned and private blockchains can handle a higher volume of transactions with lower latency. This scalability and efficiency make them a potential option for enterprise applications that require fast and reliable transaction processing without the bottlenecks often seen in permissionless networks.
Compliance with regulations
The centralized governance of permissioned blockchains can allow for easier enforcement of regulatory requirements, such as GDPR and financial regulations. Organizations may choose to ensure that their blockchain operations comply with legal standards, offering greater peace of mind in highly regulated industries.
Streamlined governance
Permissioned, private blockchains benefit from centralized or consortium-based governance, enabling quicker and more efficient decision-making. This streamlined process allows organizations to adapt swiftly to changes in business needs or regulatory environments without needing widespread consensus from a large, decentralized community.
Cons of Permissioned Blockchains
Despite their strengths, permissioned blockchains also come with notable drawbacks that potential adopters must weigh carefully.
Centralization risks
The centralized nature of permissioned blockchains introduces the risk of single points of failure. If the central entity is compromised, it can jeopardize the entire network, leaving it more vulnerable to attacks compared to decentralized systems.
Limited transparency and openness
Permissioned and private blockchains often sacrifice transparency for privacy and control. While this can be beneficial for protecting sensitive information, it limits the openness of the network, making it harder for external parties to audit or verify the blockchain's operations.
Vetting new participants
Managing a private, permissioned blockchain can become complex as the number of participants increases. The central authority must ensure that the blockchain remains secure as more entities join, presenting a challenge unique to this network type. Additionally, the need to verify and authorize new participants can slow down the process of scaling the network, limiting its ability to accommodate rapid growth.
Vendor lock-in
Permissioned networks can become dependent on a particular vendor's technology and services, which could limit an organization's flexibility. For example, if a governing body decides to transition to a different blockchain platform or modify the existing one, the process can be costly and time-consuming.
Advantages of Permissionless Blockchains
Permissionless blockchains bring unique advantages rooted in openness and decentralization, fueling innovation across the crypto ecosystem.
True decentralization
Permissionless blockchains offer full decentralization, without a lone entity controlling the network. This trustless system relies on decentralized consensus mechanisms like PoW and PoS, allowing participants to transact without needing to trust one another or a centralized authority, ensuring higher levels of autonomy and security.
Security through consensus
The security of permissionless blockchains is enhanced by their decentralized nature. Consensus mechanisms like Proof-of-Work and Proof-of-Stake make it extremely difficult for any single entity to compromise the network, providing a resilient defense against attacks and preserving the immutability of transactions.
Community innovation
Permissionless, public blockchains encourage open innovation by allowing anyone to participate in the network's development and use. This inclusivity means a vibrant community of developers and users can continuously contribute to the evolution of the blockchain, potentially leading to technological advancements and diverse applications.
Censorship resistance
The decentralized structure of permissionless blockchains makes them highly resistant to censorship and tampering. Without a central authority, no one person can alter or control the data on the blockchain, ensuring the integrity of the ledger and protecting against malicious interference.
Limitations of Permissionless Blockchains
However, permissionless blockchains face challenges that can limit their scalability, governance, and mainstream adoption.
Scalability and energy consumption
Permissionless blockchains face significant challenges in scalability due to their resource-intensive consensus mechanisms. Proof-of-Work blockchain networks like Bitcoin consume large amounts of energy and struggle to process transactions quickly, leading to slower performance and higher costs.
Regulatory and legal uncertainty
The decentralized and global nature of permissionless blockchains complicates regulatory compliance, as they pose new questions to traditional legal frameworks. This can create legal uncertainty for participants and poses challenges for governments attempting to enforce regulations on decentralized systems.
Governance and hard forks
Governance in permissionless and public blockchains can be contentious, as decisions require consensus from a large and diverse community. Disagreements can lead to hard forks, where the blockchain splits into two separate networks, causing fragmentation and potential instability within the ecosystem.
51% attacks
While permissionless blockchains are generally secure, they are not immune to security risks like a 51% attack. A well-known vulnerability in PoW blockchains, this hack can occur when an entity controls more than 50% of the network's hashing power.
This person (or persons) could then manipulate the blockchain in ways like double-spending coins or blocking new transactions. Although such attacks are rare and difficult to execute, they remain a potential risk, especially for networks with lower user participation.
Use Cases: Permissioned vs Permissionless blockchains
Permissioned and permissionless blockchains serve different purposes depending on the industry. Below are some of the most common applications across sectors.
Financial services and banking
- Permissioned: Favored by banks for privacy, compliance, and secure transaction processing.
- Permissionless: Powers DeFi platforms with transparency and accessibility, though scalability and regulation remain hurdles.
Supply chain management
- Permissioned: Enables private, controlled tracking of goods among trusted participants.
- Permissionless: Useful for public verification but limited by privacy and scalability concerns.
Decentralized finance (DeFi)
- Permissioned: Rarely used except where regulation is essential.
- Permissionless: Core of decentralize finance, enabling intermediary-free decentralized exchanges, lending, and more.
Government and public services
- Permissioned: Ideal for secure, regulated use cases like identity, voting, and land registries.
- Permissionless: Can provide transparency for public records but faces governance and compliance barriers.
Digital identity and data management
- Permissioned: Supports compliant, private identity systems with controlled access.
- Permissionless: Allows user-owned identities while raising privacy and regulatory challenges.
Healthcare and medical records
- Permissioned: Best for securely sharing medical data while meeting HIPAA/GDPR standards.
- Permissionless: Enables patient-owned health records though faces adoption limits due to privacy concerns.
Real-World Case Studies
Let's explore some real-world case studies that highlight how these technologies are being used in different industries.
IBM Food Trust: Permissioned blockchain in supply chain management
IBM Food Trust is a blockchain-based platform designed by IBM to improve transparency and traceability in the food supply chain. The platform is built on the Hyperledger Fabric, a permissioned blockchain framework that allows multiple organizations to participate in a secure and controlled environment.
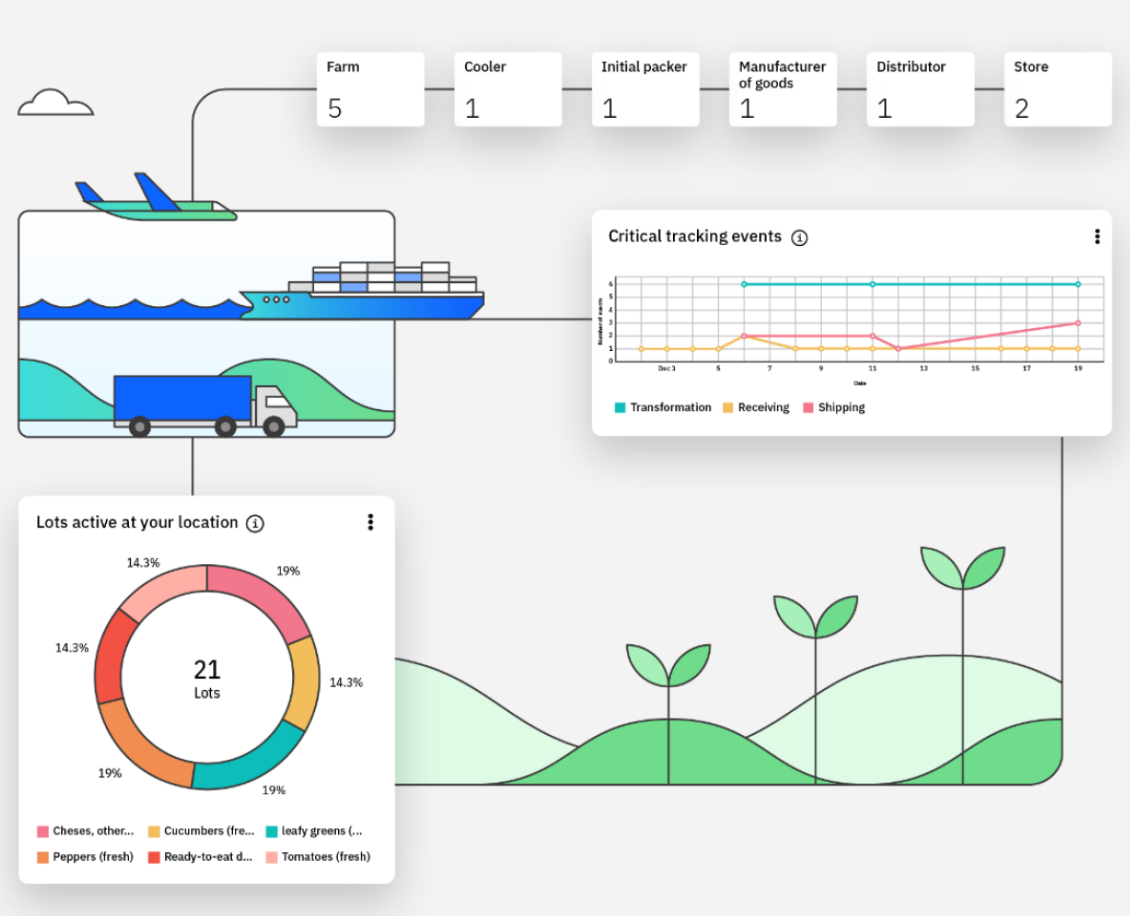
IBM Food Trust enables participants to track the journey of food products from farm to table, providing real-time data on the origin, condition, and movement of goods. Its permissioned platform allows IBM to select only authorized participants, such as farmers, distributors, retailers, and regulators, to access the network. This controlled access helps to protect sensitive data while ensuring that all parties involved have accurate and up-to-date information.
The platform has been adopted by major companies like Walmart, Nestlé, and Dole, who use it to improve food safety, reduce waste, all while attempting to enhance consumer trust. For example, Walmart uses IBM Food Trust to trace the origin of fresh produce, enabling the company to quickly identify and remove certain products from its shelves if necessary.
Bitcoin and cross-border payments: Permissionless blockchain in financial services
Bitcoin, the first and most well-known cryptocurrency, operates on a permissionless blockchain and has revolutionized the way people think about money and financial transactions. One of the key use cases for Bitcoin (BTC) is cross-border payments, where it offers a faster, cheaper, and more transparent alternative to traditional banking systems.
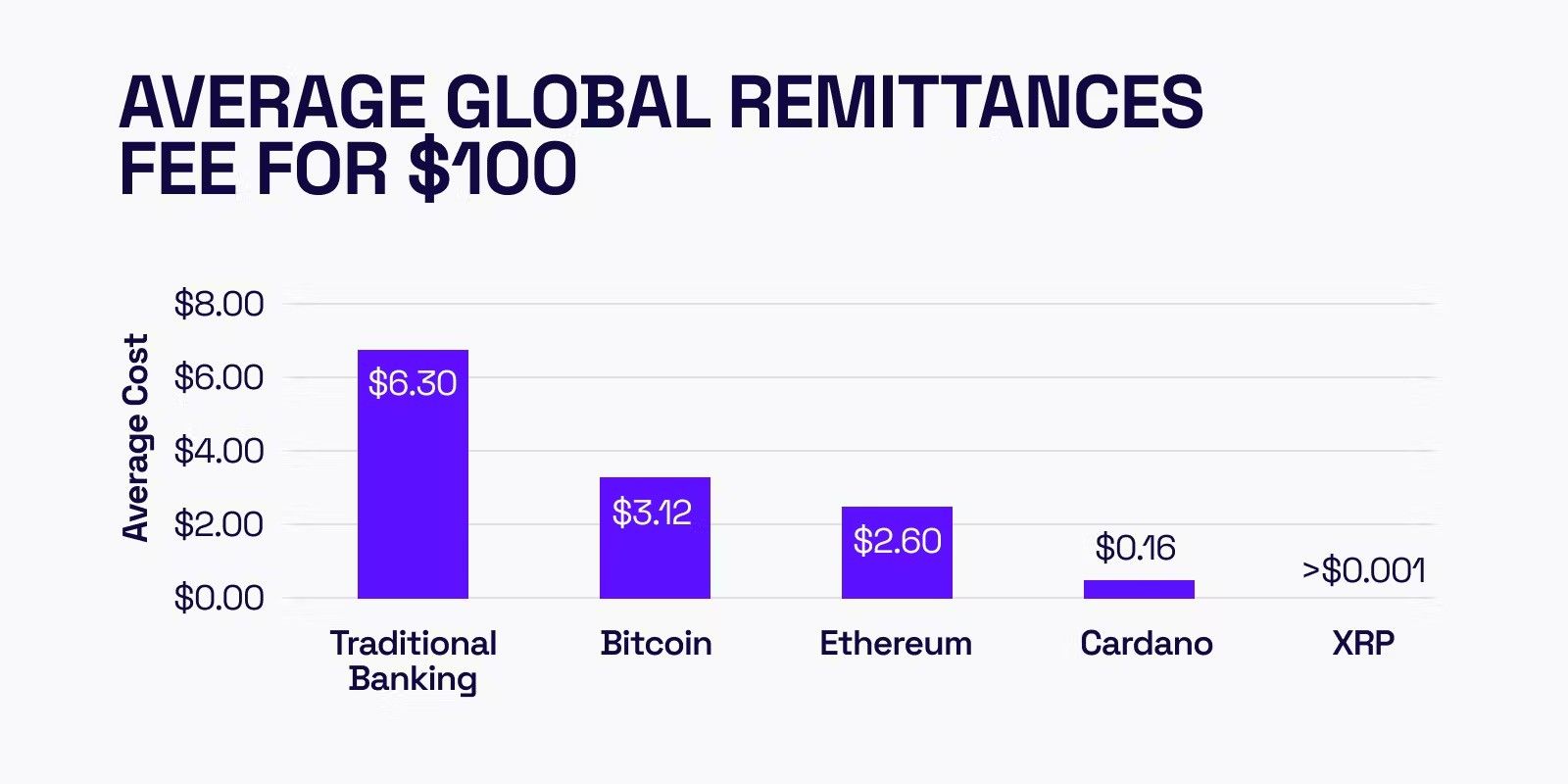
Traditional cross-border payments can be slow and expensive, often involving multiple intermediaries, each taking a fee for their services. In contrast, Bitcoin allows users to send money directly to anyone, anywhere in the world, without relying on third party institutions. Transactions are processed within minutes, and the fees are typically much lower than those charged by traditional payment systems.
Bitcoin's permissionless blockchain ensures that all transactions are transparent and verifiable by anyone, providing a high level of trust and security. This feature is particularly valuable in regions where access to traditional financial services is limited or where trust in the local banking system is low.
Which type of blockchain should I use?
The right blockchain choice depends on your priorities:
If privacy, compliance, and control are critical, such as in enterprise or government applications, a permissioned blockchain is typically best.
If decentralization, openness, and transparency are more important, like in DeFi, NFTs, or other Web3 projects, a permissionless blockchain is the stronger fit.
Scalability is also a factor: permissioned networks often handle smaller participant pools more efficiently, while permissionless networks may face performance challenges but continue to evolve with Layer-2 and scaling solutions.
Frequently Asked Questions (FAQs)
What is the difference between permissioned and permissionless blockchains?
The main difference between the two blockchain types is access.
Permissioned blockchains restrict participation to verified members, often managed by a central authority, making them suitable for enterprises that need privacy and compliance. Permissionless blockchains are open to anyone, offering transparency, decentralization, and global accessibility.
1) Is Bitcoin permissioned or permissionless?
Bitcoin runs on a permissionless blockchain. Anyone with an internet connection can join the network, validate transactions via Proof-of-Work, and view the ledger without needing approval from a central authority.
2) Which is more secure: permissioned or permissionless blockchain?
Both offer levels of security, but in different ways. Permissioned blockchains rely on trust within a closed group of participants and custom consensus mechanisms. Permissionless blockchains depend on decentralized consensus (like Proof-of-Work or Proof-of-Stake), making them resistant to censorship and tampering.
3) What industries use permissioned blockchains?
Permissioned blockchains are commonly used in banking, supply chain management, healthcare, and government services. They are chosen for their controlled access, regulatory compliance, and ability to protect sensitive data.
4) Can a blockchain be both permissioned and permissionless?
Yes, some hybrid blockchain models combine elements of both. For example, a network might allow open participation (permissionless) for certain functions while restricting access (permissioned) for sensitive operations, creating a balance between transparency and privacy.
5) What are some examples of permissioned and permissionless blockchains?
- Permissioned examples: Hyperledger, Corda, Quorum
- Permissionless examples: Bitcoin, Ethereum, Solana, Tron
Get Started with Blockchain Networks
No matter which type of blockchain network you choose, the first step to exploring them is owning cryptocurrency.
MoonPay makes it easy to buy crypto required by different blockchains, like Bitcoin (BTC), Ethereum (ETH), USDC (USDC), and 100+ other tokens. Just enter the amount of crypto you wish to buy, and use your preferred payment method like credit/debit card, bank transfer, Apple Pay, and more.
When you decide it's time to cash out to fiat, you can sell crypto using MoonPay's off-ramp. Simply input the amount of cryptocurrency you wish to sell, and enter the details where you'd like to receive your funds.


.png?w=3840&q=90)

.png?w=3840&q=90)
