Even with dozens of billions of dollars in total value locked, DeFi (decentralized finance) is still in its early stages. There's no denying that it has created a wide array of new services, such as decentralized finance protocols, lending services, decentralized exchanges, and derivatives markets. There's also no doubt that there have been some bad actors seeking to exploit the nascent industry.
Here's some perspective: More than $3 billion worth of cryptocurrency was stolen in 2021 (a 6x increase from the previous year) and $4 billion in 2022. In 2023, over $1 billion was stolen in the DeFi space alone, though this did account for a 50% drop from the previous year.
Recently, the type of hack also flipped. Nearly a decade ago, hackers almost exclusively used on-chain means. But for the first time ever, attacks between 2023 and 2024 were performed more often through off-chain attacks.
Since the onus of keeping crypto safe in DeFi is entirely on the users, most people who lost their funds never got them back.
As new opportunities arise, so do the risks of scams and fraud. Being aware of these risks is essential to protecting your cryptocurrencies when using decentralized finance (DeFi) protocols.
In this article, we walk you through some steps you can take to help protect your digital assets in the budding world of decentralized finance.
How safe are hot wallets for storing your assets?
Hot wallets, unlike cold storage options, are connected to the internet. Basically this means they're always vulnerable to hackers who can steal your coins. While they're great for transactions and day-to-day usage, hot wallets are not recommended for long-term storage.
If you must use a hot wallet, you should choose one that is known to be reliable, and should make sure to always keep your private key safe.

Keep in mind that most hot wallets also rely on central entities for transaction verification. They use APIs from companies like Alchemy and Infura. The information fetched from these APIs is deemed to be trusted, and the wallets execute the transaction without actually confirming with the mainnet.
There are two types of hot wallets:
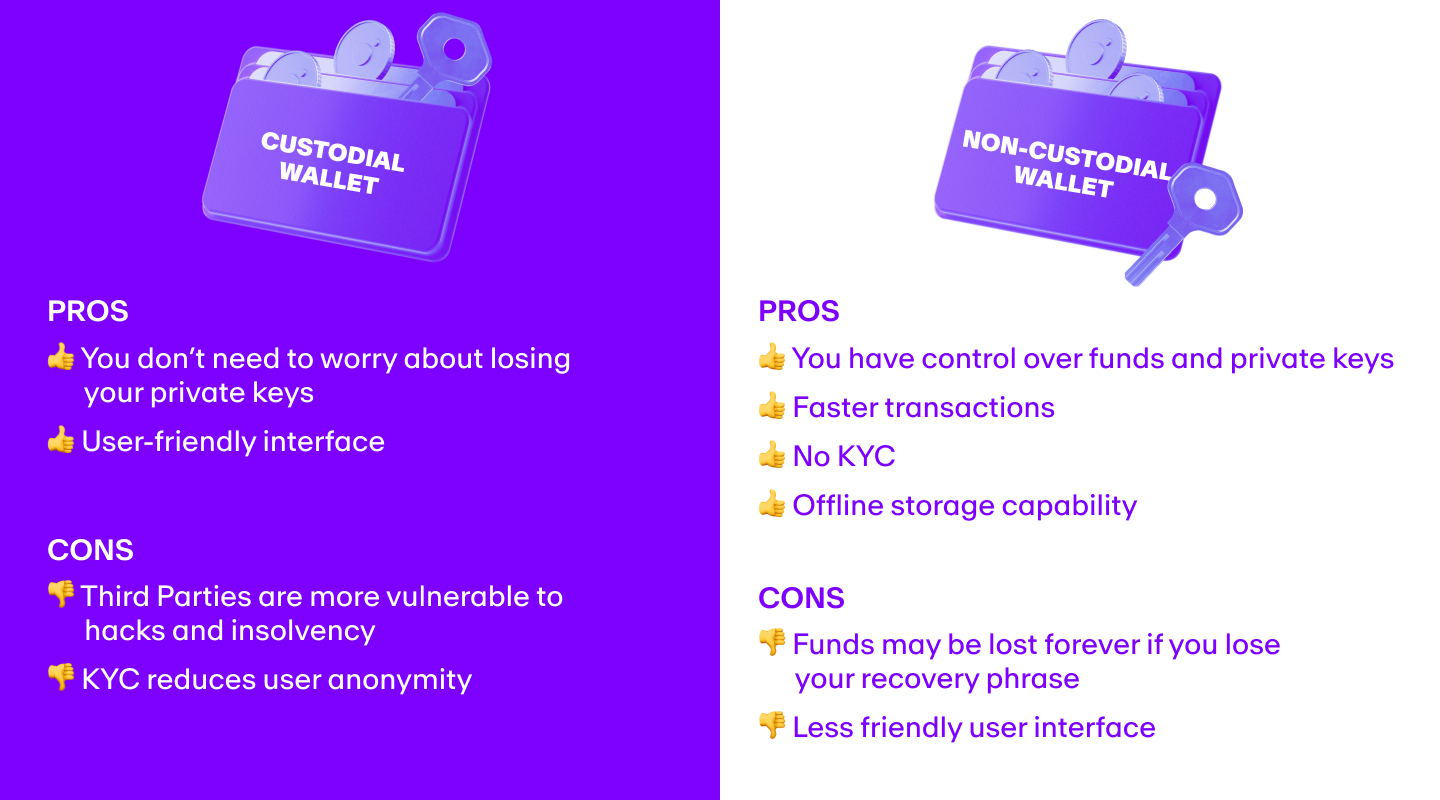
Custodial hot wallets
A custodial hot wallet is a hot wallet in which your private keys are stored by a third-party provider.
For instance, when you buy cryptocurrency through a centralized exchange like Kraken or Coinbase, the assets may still be technically under the control of the exchange, even though you own them. Centralized exchanges act as the custodian of your assets by retaining the private key of the wallet where the assets are stored.

In fact, when using a centralized exchange, your digital assets may be stored in omnibus accounts with the digital assets of other users of that crypto exchange. While you have the freedom to perform actions like trading or transferring, the custodian still has control over your assets.
The FTX debacle is a prime example of this, where users lost over $10 billion because the exchange was able to utilize user funds for other purposes without them knowing about it.
Non-custodial hot wallets
A non-custodial hot wallet is a hot wallet in which you hold your private keys. The provider does not have access to your funds, and you can transact freely without any involvement of a third party custodian.
These types of hot wallets are great if you want to engage in day-to-day crypto activities like trading, sending, and receiving. Some of the most popular non-custodial hot wallets are MetaMask, Trust Wallet, Exodus, and Phantom.
When creating a new wallet, non-custodial hot wallet software generates a "secret recovery phrase" (also known as a “seed phrase” or “mnemonic phrase”). This is a 12- or 24-word list, derived randomly from a pool of 2048 words, that gives access to your digital assets.
Even though they’re technically safer than custodial hot wallets, non-custodial hot wallets are not the best option if you are holding large amounts of cryptocurrencies and do not transact very frequently.
Because they live on your mobile or browser extensions, hackers could theoretically get backdoor access to the cryptocurrencies stored in your non-custodial hot wallet.
Are cold wallets safe for storing your assets?
Cold storage involves storing your cryptocurrencies offline in either physical or digital form. It is the way to go if you're looking for a secure way to store your crypto for the long term.
Storing in a physical form means your private keys are written on paper (also called a "paper wallet"). This method of storage makes it impossible for hackers to get to your private keys.
In most cases, however, a hardware wallet is stored on an external device similar to a USB drive and does not connect to the internet. This is a very secure way to store cryptocurrencies, but there is some compromise in terms of ease of use.
Another layer of security that almost all cold storage wallets offer is something called “mechanical keys.”
Digital hardware wallets need to be plugged into a device like a computer and connected to the web in order to execute transactions. If the computer is compromised, assets could be hacked. With mechanical keys, however, this is not possible, as the transaction would only get approved if the user physically clicks the keys (a button on the hardware device).
To learn more about different wallets, read our guide How to choose a crypto wallet
How to evaluate the security of a wallet
Hardware wallets are generally an excellent option for storing large amounts of cryptocurrencies. But since they, too, rely on code and electronics, how do you gauge their security and reliability?
Certifications are one way to evaluate a wallet's security. The most popular security certification for hardware wallets is the Evaluation Assurance Level (EAL).
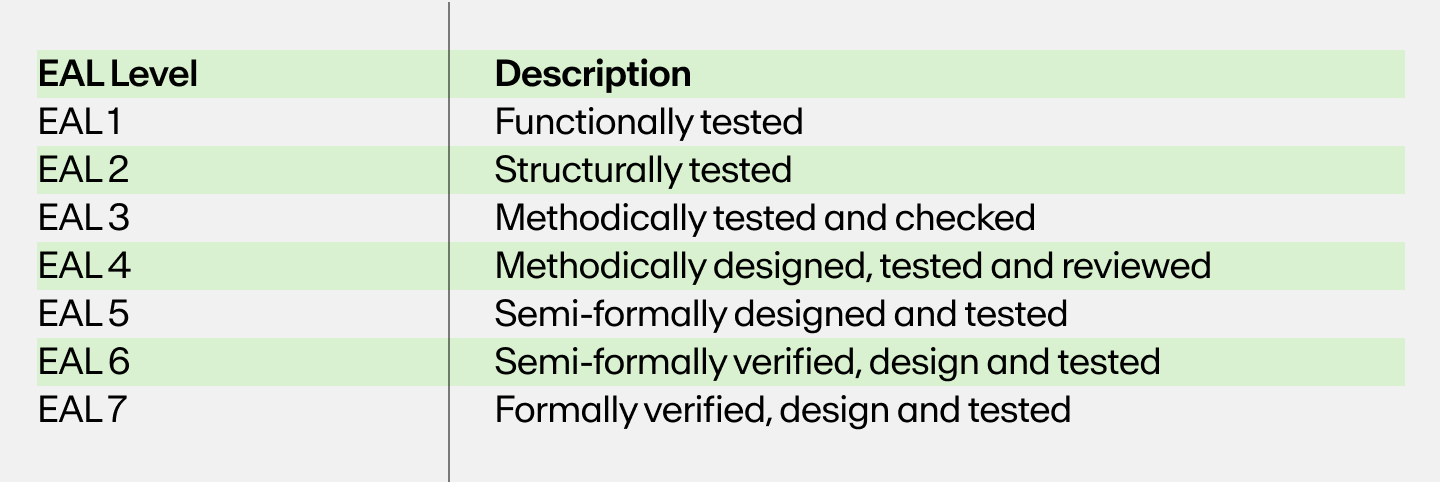
EAL is a process in which independent third-parties assess the security of wallets by testing and certifying them against various attack vectors. There are seven levels of EAL certification. A higher level of EAL, such as EAL 5+, means that the wallet has been tested against a variety of different attack types on multiple levels.
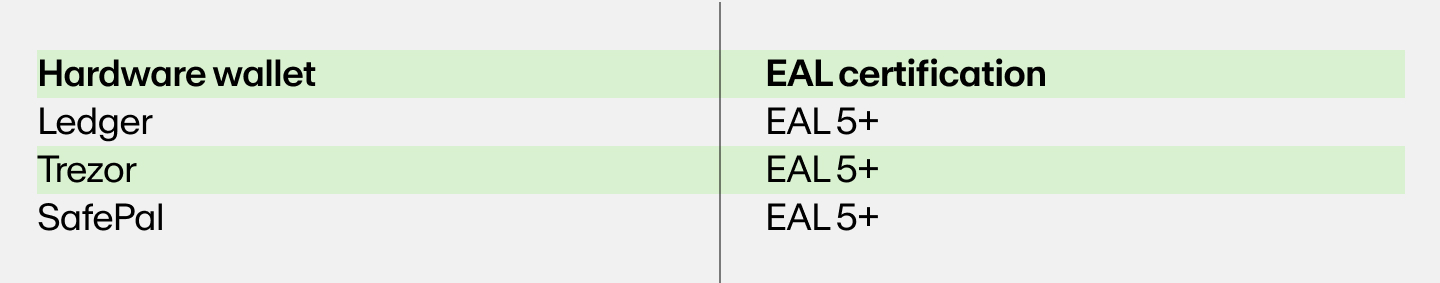
Below is a list of popular hardware wallets and their corresponding EALs:
How to move your cryptocurrency into cold storage
The most important thing to keep in mind is that the cryptocurrencies you hold may reside on different blockchains. What this means is that you will have to use a different public wallet address to access the different blockchains.
Sending your cryptocurrency to the wrong public address may result in you losing your funds forever.
For example, if you try to send BTC to a public address on the Ethereum blockchain, then your Bitcoin can no longer be retrieved.
You can move your cryptocurrency from anywhere into cold storage in just three simple steps:
- Configure your hardware wallet
- Obtain the public address
- Use the public address to withdraw
1. Configure your hardware wallet
To begin moving your cryptocurrency from exchanges or hot wallets to cold storage, you must begin by first configuring your hardware wallet to receive the particular cryptocurrency.
Most popular hardware wallets also have a user-friendly app that can be downloaded for free. For example, Ledger Live is the app used to interact with Ledger hardware wallets.
You will have to go to these apps and configure them to support the crypto you wish to store. We recommend that you refer to the instructions provided by your wallet manufacturer to configure them, as the process differs for each wallet.
To learn more about how to configure a hardware wallet, read our guide How to set up a hardware wallet
2. Obtain the public address
After configuring your wallet for the desired network (blockchain), you will get the corresponding public wallet address. Note down this public address or copy it to your computer's clipboard.
3. Use the public address to withdraw
Next, head over to the crypto exchange from where you want to withdraw your funds, go to your wallet, choose the “Withdraw” option (or other similar alternative) and paste the public address. Exchanges may send a One Time Password (OTP) to your registered email address and phone number to verify that you are the one executing the withdrawal.
Once confirmed, your funds will be deposited in your hardware wallet.
Other important security options
Keeping your cryptocurrency in cold storage is the safest way to store it.
But what if you need a different solution? You may have lots of assets, for example, or you and a group of people need to share control over a single wallet.
In these cases, Hardware Security Modules (HSMs), Multi-Signature (Multi-Sig) wallets, and Multi-Party Computation (MPC) wallets may be the way to go.
Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) are specialized hardware designed to securely store cryptographic keys, and are used in servers that host a wallet. They are a preferred enterprise option used by larger organizations, financial institutions, and governments worldwide.
Multi-Signature (Multi-Sig) Wallets
Multi-Signature (Multi-Sig) wallets are wallets that require multiple signatures from different key holders in order to execute transactions. Multi-Sigs may be ideal for large organizations and companies that do not want one signature to have full control over all digital assets.
Multi-Party Computation (MPC) Wallets
Multi-Party Computation (MPC) wallets require multiple users to authorize transactions. These wallets use a distributed computing protocol to generate private keys and create digital signatures for multiple parties.
Concluding thoughts on DeFi safety
No crypto wallet can be deemed 100% risk free. But by using a hardware wallet, enabling two-factor authentication, and regularly monitoring your transactions, you can greatly reduce the risk of your crypto being compromised. Additionally, users should only look for reputable and well-vetted DeFi protocols and exchanges before getting involved with decentralized finance.
Everything we've laid out here is important when it comes to DeFi safety. But keeping your seed phrase safe is maybe the most important steps to reducing the risk of your crypto being compromised. Write your seed phrase down on a piece of paper and store it in a safe place, or use a seed phrase backup device, and never keep it anywhere online.
Begin your DeFi journey with MoonPay
Now that you know a bit more about how to safely store cryptocurrency in DeFi, it’s time to experience crypto for yourself.
To begin, simply buy crypto using a credit card or any other preferred payment method. Then follow the instructions to complete your order.






